I've been helping a few co-workers prep for the Juniper JNCIS-ENT certification. One thing I noticed is that while there is plenty of older material to be found online, it's hard to find information on enabling Port Security features using the modern ELS syntax. The new JNCIS-ENT exam (JN0-347) uses ELS syntax, so I wrote down some information myself.
ELS
In case you missed it, ELS stands for Enhanced Layer 2 Software. Juniper introduced it in Junos 13.2 for EX- and QFX-switches to provide a more uniform syntax across the product line; it's now similar to layer-2 configuration on MX routers.
Check this page for an overview on what has changed. Most of it is fairly straightforward, but some features (like DHCP Snooping) require a little more explanation.
Layer-2 Security features
In case you're wondering: yes, you really need layer-2 security. Unless you take the necessary precautions, it's quite easy to perform a man-in-the-middle or denial of service attack in a switched layer-2 environment.
There is a whole bunch of layer-2 security features supported on Juniper switches for both IPv4 and IPv6, but for this post I'll limit myself to DHCP Snooping and its related features for IPv4.
DHCP Snooping
DHCP Snooping means inspecting DHCP packets traversing the switch, and then deciding whether to allow or drop that packet. There's a detailed description better than I can provide over at the Packet Pushers blog.
There are two main security benefits to inspecting DHCP traffic:
- You can check whether any DHCP offers are coming from a trusted DHCP-server; and
- You can create a table with valid MAC/IP bindings based on those DHCP offers.
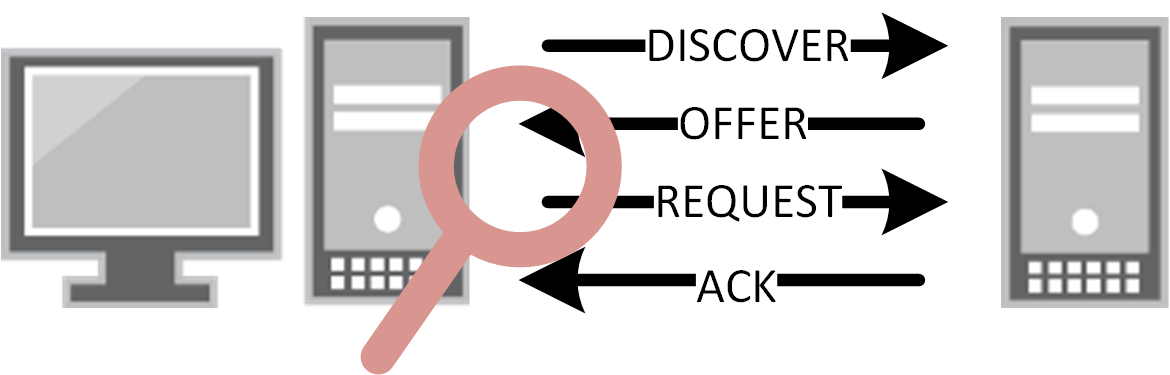
The first point is pretty straightforward. The DHCP exchange consists of four steps:
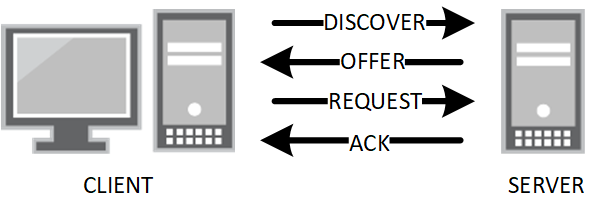
A client should only sent Discover and Request packets; the DHCP server is the only one allowed to send Offers and Acks. Any Offer packets from ports where you would not expect them can be dropped. This means that your network won't go down when someone decides to bring their home router for some extra wireless coverage and plug in the LAN port (or do something more nefarious.
The second point is not particularly useful of itself, but once you have a list of valid MAC/IP bindings you can use that table to perform some additional security checks: IP Source Guard and Dynamic ARP Inspection.
IP Source Guard
It's pretty easy to change the source IP address for outgoing IP traffic. When you do this, any replies to your packets are sent to the fake IP instead of to your real IP. This technique is widely used in DDOS attacks. To combat this, the IETF has published guidelines for ISPs to implement filtering on the edge of their networks to restrict forged traffic: BCP 38. This eases the problem for the internet at large, but it's not applicable to layer-2 switched networks.
However, now that we have snooped the DHCP packets, we have a table connecting IP addresses to the switchport they belong to. IP Source Guard uses the DHCP Snooping table to drop any packets with source IP addresses that are spoofed.
Dynamic ARP Inspection
Dynamic ARP Inspection (DAI) can protect your network against ARP Spoofing. ARP Spoofing means answering ARP requests for IP addresses that you don't own. This would allow you to perform a Man-in-the-Middle attack by letting other machines on the LAN think you are the default gateway. This is actually surprisingly easy to do.
The DHCP Snooping table contains MAC addresses coupled to the IP address that are actually assigned to these hosts. By inspecting ARP packets and checking them against this table, the switch can drop any ARP replies that contain invalid IP/MAC bindings.
Configuration
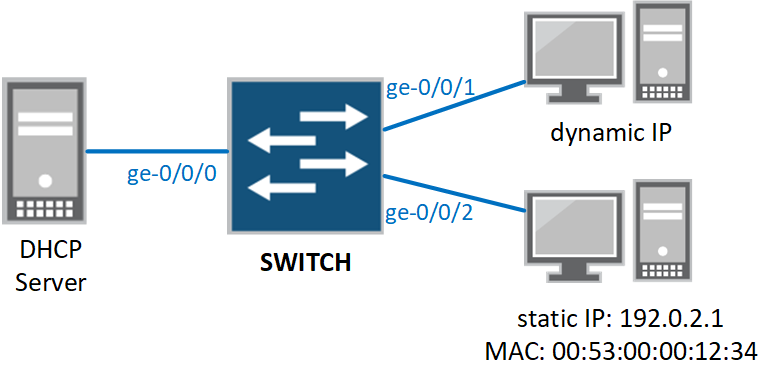
The demonstrate the configuration of DHCP Security in ELS, we're going to use a very straightforward sample topology:
Enabling DHCP Snooping
Both IP Source Guard and Dynamic ARP Inspection require a DHCP Snooping table, so you have to configure DHCP Snooping first. Prior to Junos OS 17.1R1, you actually cannot enable DHCP-snooping itself. This is a change from non-ELS Junos, where it is possible. Instead DHCP Snooping is enabled automatically when you configure any of the following DHCP Security options:
- Dynamic ARP inspection (DAI)
- IP source guard
- DHCP option 82
- Static IP
From release 17.1R1 onward, you can enable DHCP Snooping on its own:
vlans {
vlan-name {
forwarding-options {
dhcp-security;
}
}
}
Enabling IP Source Guard and Dynamic ARP Inspection
IP Source Guard and Dynamic ARP Inspection are enabled on a per-VLAN basis. This is pretty straightforward:
vlans {
vlan-name {
forwarding-options {
dhcp-security {
arp-inspection;
ip-source-guard;
}
}
}
}
Keep in mind that this will also automatically enable DHCP Snooping.
Trusted Ports
At this point, we still need to exempt our DHCP server from DHCP Snooping, otherwise all DHCP Offers will be dropped by the switch. We do this by configuring the port as "trusted". Trunk ports are automatically trusted in Junos, but our server is connected to an access port so it requires some more configuration:
vlans {
vlan-name {
forwarding-options {
dhcp-security {
group DHCP-server {
overrides {
trusted;
}
interface ge-0/0/0.0;
}
}
}
}
}
Static Bindings
In our sample topology, we have one client with a static IP address. This client will not send DHCP requests, so its IP and MAC addresses will not be entered in the DHCP Snooping table. As a result, IP Source Guard and Dynamic ARP Inspection will drop all traffic from this client.
We can fix this by setting the interface to "trusted" like we did with the DHCP server, but in general we do not trust our clients. The solution is to set a static MAC/IP binding:
vlans {
vlan-name {
forwarding-options {
dhcp-security {
group static-client {
interface ge-0/0/2.0 {
static-ip 192.0.2.1 mac 00:53:00:00:12:34;
}
}
}
}
}
}
Combining all these, we have a basic DHCP Snooping configuration for our sample topology:
vlans {
vlan-name {
forwarding-options {
dhcp-security {
arp-inspection;
ip-source-guard;
group DHCP-server {
overrides {
trusted;
}
interface ge-0/0/0.0;
}
group static-client {
interface ge-0/0/2.0 {
static-ip 192.0.2.1 mac 00:53:00:00:12:34;
}
}
}
}
}
}
If you want to know more about these and all the other options you can enable, check the Juniper documentation on dhcp-security.